Cyber security in Mergers & Acquisitions, Protecting What Matters Most?
Everyone’s talking about securing the digital landscape but let’s be brutally honest, you can’t protect what you can’t see.
Without complete visibility into your environment, safeguarding your most valuable assets becomes nearly impossible. And yet, only a small percentage of organisations maintain a clear, up to date inventory of their assets and their security posture. This gap leaves businesses dangerously exposed especially during high impact events like mergers and acquisitions (M&A).
As organisations grow, they often acquire or merge with other businesses to expand their market share, eliminate competition, or complement their existing product or service offerings. However, with each acquisition comes a complex web of inherited technologies, legacy systems, and unknown cybersecurity risks that can quietly erode the value of the entire transaction.
The Overlooked Risk
In most M&A scenarios, due diligence focuses heavily on financials, brand equity, and leadership integrity. Depending on the industry, might also include checks for ethics violations, government dealings, anti-bribery compliance, emissions and waste controls, or modern slavery concerns.
Still, cybersecurity often remains an afterthought both before and after the deal is signed.
Having seen this from both sides of the table, I can confidently say there’s still a long way to go in maturing cybersecurity practices during M&A. A solid cyber due diligence process must go beyond a quick scan of compliance policies or asset spreadsheets.
What if you acquire a business and inherit an entire operational technology (OT) environment that hasn’t been patched in years?
That’s not hypothetical that’s a threat. A costly one.
Let’s not forget the real world consequences. July 19, 2024, when CrowdStrike’s Falcon update for Windows hosts caused global system crashes due to a single defect. Now imagine inheriting hundreds or thousands of endpoints like that with no awareness or plan to manage them.
A clean, secure, and compliant cybersecurity posture supported by updated policies, audits, and incident response procedures should be a foundational element of any M&A strategy.
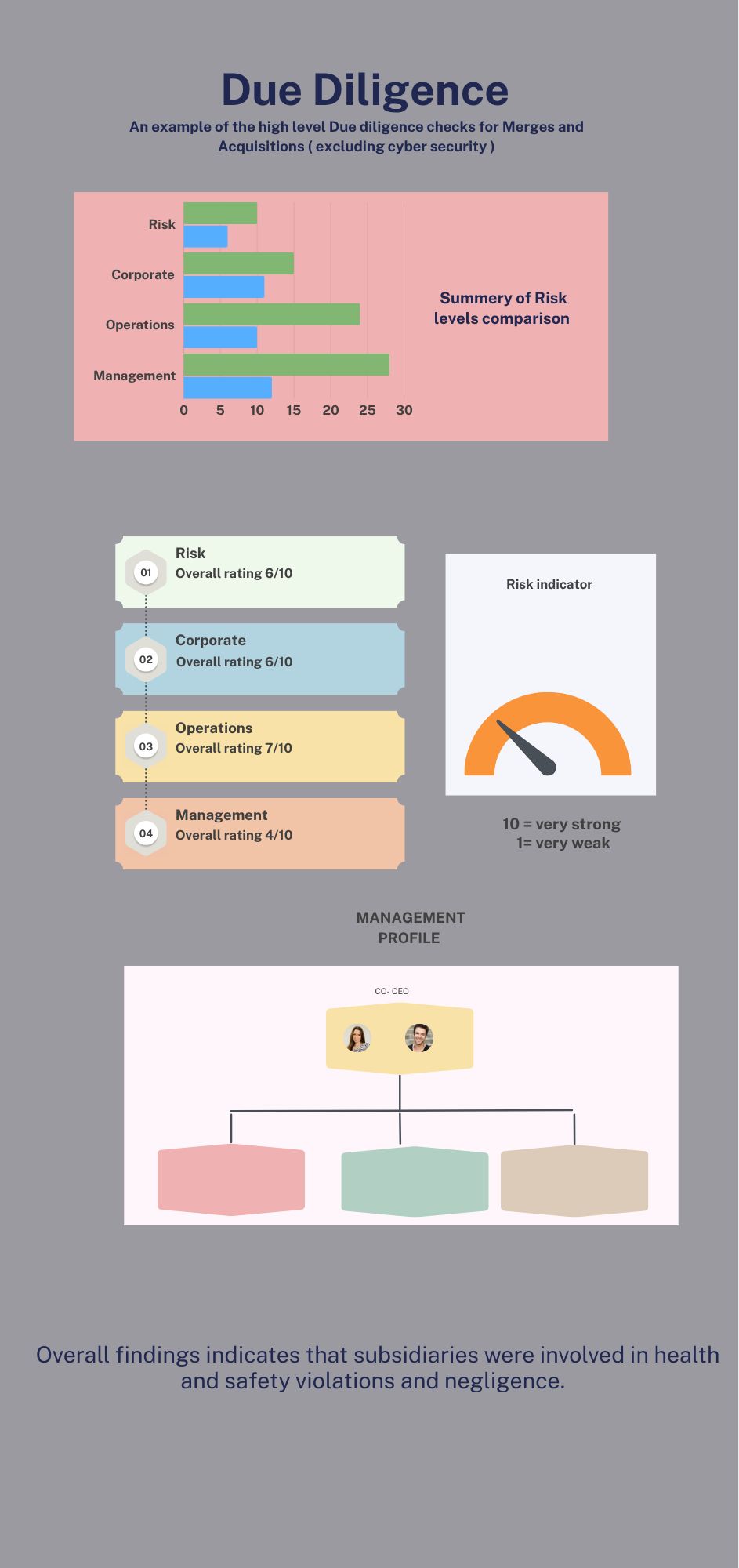
Real life scenario: A pharmaceutical device manufacture merging with a smaller device manufacture, conducted the due diligence checks for the board, however, we came crossed some challenges in MEA. By creating a table top workshops for both parties to break the cultural and language barriers, we discovered the underlying risks and openly discuss the risk mitigation process.
Before the M&A Deal: Laying the Groundwork
At the earliest stages of the M&A lifecycle, the acquiring company must take proactive steps to assess the cybersecurity maturity of the target organisation. This includes:
Understanding existing security controls in-depth account of where the gaps and vulnerabilities exist.
Evaluating the cybersecurity culture, including employee awareness, behaviour, language and cultural practices.
Performing regulatory compliance assessments, especially in industries like finance, critical infrastructure, defence, energy and healthcare.
Deep dive of assessing third-party/supply chain risks - often the threat will be the third parties not having the right data governance or the cyber awareness mindset.
Risk is inherent to any business decision, but knowing your risk tolerance and identifying whether the target company falls within acceptable limits is critical. A comprehensive cybersecurity risk assessment should:
Identify potential vulnerabilities and their financial impacts to the company.
Evaluate current and historic security incidents, lessons learned and steps taken for prevention.
Include passive threat intelligence gathering and public data monitoring.
Even a rumour of a merger can make both companies more attractive targets to attackers. A successful breach during this phase could cause significant repetitional and financial damage.
During the M&A Process: Managing the Transition
Once the deal moves into the negotiation and execution stages, integration planning begins. The acquiring firm must determine the type of integration full, partial (hybrid), or soft and assess the corresponding cyber security implications.
Key actions include:
Clear definition of roles and responsibilities between both parties.
Standardising security policies and procedures with an open mindset to understanding and respecting different cultural and language barriers.
Conducting in depth security assessments of the target company’s environment.
Discovering an undisclosed breach at this point can severely undermine trust and delay or derail the deal. That’s why pressure to close quickly should never come at the cost of due diligence.
At this stage, many companies engage external cybersecurity firms with M&A experience to conduct deep dive assessments, including:
Penetration testing
Vulnerability scans
Active threat hunting
Subject matter advisory
Tools like identify access management, endpoint detection and response (EDR), security information and event management (SIEM), continuous monitoring, and advanced threat detection become indispensable particularly as integration efforts begin and network complexity increases. M&A related cyber sabotage, espionage, and disruptions are all real risks.

Post-M&A: Maintaining Vigilance
Once the deal is closed, integration is in full swing but the work is far from over.
Post-acquisition is a high-risk period that requires:
Defining and monitoring Key Risk Indicators (KRIs)
Clear communication, and visibility.
Continuous monitoring for emerging threats
Addressing any remaining vulnerabilities quickly
Security measures must be regularly evaluated for effectiveness. This includes integrating incident response plans, aligning IT policies, and ensuring all teams understand roles and responsibilities during a cyber event such as a DDoS attack or data breach.
To maintain resilience:
Conduct simulated cyber drills and phishing tests
Update and test incident response plans
Continue monitoring with 24/7 threat detection systems
The acquiring CISO (or equivalent leader) must ensure that cybersecurity standards and best practices are consistently enforced across the newly merged organisation.
Final Thoughts: Cybersecurity as a Strategic Priority
A successful M&A depends not just on operational and financial synergy, but also on the strength of the combined cybersecurity posture. Cyber risk doesn’t start after the deal it begins the moment the merger is rumoured.
To succeed in today’s high-risk environment, companies undergoing M&A must:
Assess their own cybersecurity maturity
Evaluate the target firm’s IT infrastructure and security posture
Ensure high levels of security during integration
Prepare for attacks and establish resilience post-acquisition
Given the complexity of M&A, organisations regardless of size often benefit from engaging specialised IT service providers. These experts conduct internal and external audits, bring deep industry experience, and reduce cyber risks effectively.
Organisations with a robust cybersecurity strategy ,including regular patching, automation, application security, and SIEM tools combined with a healthy cultural awareness can navigate the M&A process faster and with significantly less risk.
Cybersecurity isn’t just an IT issue. It’s a business imperative and in the world of mergers and acquisitions, it could be the difference between success and failure.

